By Courtney E. Howard
WASHINGTON - Systems integrators and commercial-off-the-shelf (COTS) vendors are combining technologies to demonstrate a secure multiple independent levels of security (MILS) software architecture that protects military and intelligence communications networks on the global information grid (GIG).
The Open Group, headquartered in San Francisco, drew nearly 400 information technology professionals and technology experts to its Architecting to the Edge conference in Washington, where they discussed the issues, challenges, and innovations involved in getting the right information to the right people at the right time.
Systems involving a distributed architecture, the interaction of a multitude of services, fault tolerance, and real-time operation are considered to be on the edge, according to officials of The Open Group.
One conference session of particular value to the defense industry, “MILS Architecture and Demonstrations,” was well attended by more than 200 members of the defense community, including personnel from the Department of Defense (DOD), National Security Agency (NSA), Defense Information Systems Agency (DISA), and the Department of Homeland Security (DHS).
The Air Force Research Laboratory (AFRL), systems integrators Raytheon Co. in Waltham, Mass., and Lockheed Martin Corp. in Bethesda, Md., middleware developer Objective Interface Systems in Herndon, Va., and COTS software vendors Green Hills Software in Santa Barbara, Calif., LynuxWorks Inc. in San Jose, Calif., and Wind River Systems in Alameda, Calif., contributed to the session’s presentations, demonstrations, and question-and-answer panel discussion.
The session opened with an address by U.S. Air Force Lt. Col. Brett Telford, deputy director of the DOD’s Open Systems Joint Task Force, who stressed the critical need to secure warfighting systems in a network-centric environment.
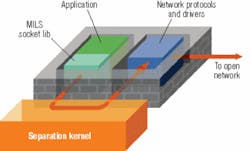
Flowers’s words were brought home by the event that followed: the first public demonstration of a simulated airborne reconnaissance mission, directed by Raytheon. The simulation employed a MILS workstation to present an on-screen display of animated reconnaissance aircraft as they traveled to, passed over, and gathered imagery of a set of predetermined targets.
Arousing applause from the audience, the aircraft were simulated on embedded processors running MILS separation kernels from competing vendors. The MILS-compliant real-time operating systems (RTOS) used in the real-world demonstration included COTS software systems from Green Hills Software, LynuxWorks, and Wind River, as well as MILS middleware from Objective Interface Systems. A Linux workstation represented the GIG.
“That commercial products based on the MILS architecture have become available is a major step forward,” says David Lounsbury, vice president of government programs at The Open Group.
In the end, products from Green Hills Software, LynuxWorks, and Wind River, as well as MILS communications middleware from Objective Interface Systems and commercial operating systems like Linux, worked in tandem in a real-world scenario.
At the same time, multiple levels of data having different security classifications were successfully protected and separated using the commercial communications infrastructure made up of readily available network hardware and software solutions.
“This has huge benefits for military and intelligence organizations by enabling the secure and safe separation of classified, highly classified, and top-secret information,” Lounsbury continues. “Such work has direct application in … organizations for which security breaches are not an option.”