COTS-based trusted computing: getting started in next-generation mission-critical electronics
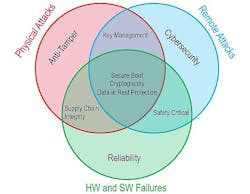
Trusted computing involves technologies and techniques that protect mission-criticalembedded electronics from physical and remote attacks and from hardware and software failures. Through anti-tamper methodologies and avionics safety certifiability processes, trusted computing also ensures that a system will only execute what is intended and nothing else.
In the aerospace and defense market, solutions based on embedded hardware frequently play in critical applications involving sensitive and classified information; the goal being to operate these systems with complete confidence that they are secure and uncompromised.
Trusted computing also delivers confidence that any critical data or intellectual property (IP) will not benefit U.S. adversaries if the hardware falls into enemy hands. Anti-tamper defines the set of solutions to protect against physical attacks on the system.
Cyber security defines those protections fielded against remote attacks. System reliability results from activities designed to mitigate hardware and software failures. Approaches for providing trusted computing for anti-tamper, cyber security, and reliability can intersect in various ways.
For example, reliability, includes supply chain integrity, which ensures that supplied parts and software don’t introduce vulnerabilities into the system.
Another important element of supply chain integrity is to activate a counterfeit electronics parts control plan in accordance with the AS5553B and AS6174 anti-counterfeit part processes.
The effectiveness of these efforts can have a direct effect on the anti-tamper portion of trusted computing because maliciously altered or counterfeit devices can be weak links that an adversary might exploit to intrude into a system.
When it comes to manned and unmanned aircraft operating in domestic airspace, safety certifiability processes can play a part in trusted computing. These processes can help designers develop commercial off-the-shelf (COTS) avionics hardware demonstrated to be safe for use in domestic airspace.
Safety certifiable processes help speed the design and COTS avionics hardware, as well as the eventual safety certification of the avionics hardware, by providing supporting artifact packages for these products, which otherwise can take years and millions of dollars to develop. Certifiable products can meet the required DO-254 Design Assurance Level (DAL) for hardware, and DO-178C DAL level for software.
Safety certifiable processes can help COTS vendors reduce design risk greatly, and deploy avionics solutions quickly and cost-effectively that are certified safe for operating in domestic controlled airspace.
This series of columns will consider elements that make up an effective trusted computing strategy, including anti-tamper technology protection, cyber security data protection for software and algorithms for data at rest and data in transit, and reliability processes for protecting the COTS embedded computing and electronics supply chain.
This is the first in a series of columns that will address the use of open-standards COTS technologies that address trusted computing in deployable embedded systems for aerospace and defense applications.
Related: Trusted computing hardware: what you need to know
To ensure that these approaches are as strong and effective as possible, COTS vendors and systems integrators should begin a conversation about what steps are available to meet anti-tamper, cyber security and reliability requirements as early as possible in the design stage. It’s always more difficult to add security by backfilling than it is to build it in from the ground up.
In future columns, we will discuss such topics as data encryption, trusted and secure booting, protection of data-at-rest, protection of data-in-transit, and safety certifiability for airborne avionics systems.
Trusted computing doesn’t have an end point; it’s an ongoing process that evolves with new threats and new technologies. This column will provide a platform for shining light on known and emerging options for keeping embedded systems secure.
Steve Edwards is technical fellow at the Curtiss-Wright Corp. Defense Solutions Division in Ashburn, Va. His email address is [email protected]. Learn more about trusted computing at Curtiss-Writh online at www.curtisswrightds.com/technologies/trusted-computing.
Ready to make a purchase? Search the Military & Aerospace Electronics Buyer's Guide for companies, new products, press releases, and videos