Securing safety-critical software for avionics and other mission-critical systems
PALM HARBOR, Fla. – Many military systems host multiple applications, and those applications can be at varying security levels. To represent trusted computing, however, an application must not be able to see the contents of another application’s data (confidentiality), change the data of another application (integrity), or cause another application or its data to become inaccessible for a period of time (availability) -- even when the separate applications are at the same security level.
When applications are authorized to share data, they must share data only that the sender is authorized to send and the receiver is authorized to receive, and the data must flow over an authorized communications channel.
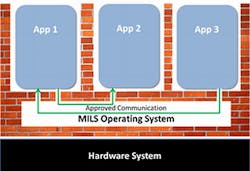
The base component of software security is an operating environment that prevents software applications from interacting except through authorized channels. The general solution is a multiple independent levels of security (MILS) operating system, which uses a separation kernel to isolate applications and their data into different security domains and provide mechanisms for permitting authorized communication across domains.
When applications at different security levels communicate to share data, the MILS operating system should include support for hosting multi-level secure (MLS) applications. A typical MLS application is a cross-domain solution (CDS) that filters specific information flow from higher security levels to lower security levels.
Related: Securing safety-critical software for avionics and other mission-critical systems
Best practices using open-systems standards dictate that systems engineers should implement security at several levels -- also known as defense in depth -- such that any vulnerability at one level can be caught at another level. Securing communications among separate applications leads to implementing additional security mechanisms in the communication protocol. Those mechanisms should include:
-- authentication to verify the identity of an application or user;
-- access control to enforce policy decisions on what operations an authenticated application or user can perform;
-- integrity to assure the accuracy and completeness of the communication so that it cannot be modified in an unauthorized manner; and
-- confidentiality to protect information from unauthorized access and disclosure.
Although systems engineers can design-in such secure communications using low-level operating system mechanisms like the sockets API, the level of effort and complexity for that approach generally leads to unacceptably high risk, high cost, and low application portability.
A better solution is to use secure communications middleware such as the Data Distribution Service (DDS) standard from the Object Management Group (OMG) in Needham, Mass., including the DDS Security specification.
Related: Trusted computing: application development, testing, and analysis for optimal security
DDS is a modern communication middleware with a publish/subscribe model that includes multicast communication, dynamic discovery, no single point of failure, and proven interoperability.
The base DDS standard provides a level of security through its brokerless, peer-to-peer architecture. It contains the concepts of domains and partitions that provide a separation mechanism for the system integrator.
The specification also includes type information for each piece of data communication, which a security monitor can use to inspect and filter communication between domains. The DDS security specification adds security plug-in APIs for authentication, access control, cryptography, and logging. DDS security features are integrated with the DDS network protocols -- not simply layered on top of a transport layer, which gives the application developer flexibility to configure security features on a topic-by-topic basis.
An example implementation of a MILS operating system with DDS layered on top is the INTEGRITY-178 safety- and security-critical real-time operating system (RTOS) from Green Hills Software in Palm Harbor, Fla., integrated with CoreDX DDS Secure communications middleware from Twin Oaks Computing Inc. in Castle Rock, Colo.
The INTEGRITY-178 RTOS is a separation kernel, and is certified to the Separation Kernel Security Profile (SKPP) defined by NSA and NIST. The SKPP is a security requirements specification for separation kernels suitable for the most hostile threat environments, and INTEGRITY-178 is certificated to the highest evaluation assurance level (EAL 6+) for general software products.
As part of fulfilling the requirements of the SKPP, INTEGRITY-178 supports information flow control, resource isolation, trusted initialization, trusted delivery, trusted recovery, and audit capabilities. INTEGRITY-178 is a MILS operating system that also provides support for MLS applications so that it can host cross domain solutions.
The CoreDX DDS communications middleware sits on top of a networking stack and the operating system, simplifying applications by streamlining the way they receive and process data. CoreDX DDS is self-contained, with no dependencies on additional pieces of software beyond the operating system and networking stack, so it works out of the box.
CoreDX DDS has a small code base, making it easy to certify for security and safety. CoreDX DDS Secure is a communication solution that includes authentication of end points, access controls, message integrity checking, and encryption.
A wide range of control and configuration options enable flexible deployment, while enabling dynamic and scalable publish-subscribe or remote procedure call communications. Together CoreDX DDS and the INTEGRITY-178 RTOS form an integrated software solution for securing and communicating between high-assurance applications.
Richard Jaenicke is the director of marketing for safety- and security-critical products at Green Hills Software in Palm Harbor, Fla. His email address is [email protected].
Ready to make a purchase? Search the Military & Aerospace Electronics Buyer's Guide for companies, new products, press releases, and videos