Creating Secure C2 Links for UAVs
By Phil Linker, FreeWave Technologies Inc.
Unmanned aerial vehicles (UAVs) are at the forefront of an evolution. Since the Federal Aviation Administration (FAA) re-authorization bill was signed in February 2012, giving the green light for commercial operation of UAVs, the industry has been abuzz with new opportunities for implementation. These unmanned systems are no longer primarily associated with war and combat situations. With a deadline of Sept. 15, 2015 for full integration into U.S. airspace, it is highly likely that UAVs will play an increasing role in our critical infrastructure operations.
Industries such as public safety, land/crop surveying and oil/gas are being eyed as key markets that can benefit from the use of unmanned systems for monitoring and surveillance. For several applications, such as wildfire monitoring and border protection, UAVs can even be used to protect people and save lives.
In July it was announced that the FAA had certified the first UAV for commercial use. According to the announcement, a major energy company in Alaska will be using UAVs to support emergency response crews with oil spill monitoring and wildlife surveillance. The UAVs utilized by the energy company will operate under the Arctic Implementation Plan released in November 2012, which is perhaps one of the most significant milestones for UAVs to date. Under the Arctic Implementation Plan small UAVs are permitted to operate for commercial use in designated “permanent operational areas and corridor routes.” By expanding into Arctic airspace, the plan aims to benefit communities located in the designated operational areas with new opportunities in scientific research, Search and Rescue (SAR), environmental analysis, fisheries and more. The areas proposed in the plan that would comply with this expansion include, the Southern Arctic Area, Bering Strait Area and Northern Arctic Area.
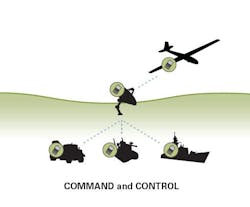
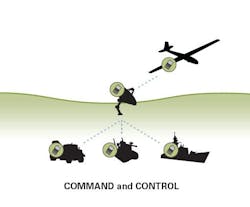
As the implementation continues to expand, airspace will naturally become more crowded. In 2011, the NAS saw more than 100,000 aviation operations per day. With the introduction of UAVs this number will continue to increase. It is going to be critical for UAVs to be operationally sound and designed with secure data transmission in mind. Safety is the top priority of the FAA for the operation of UAVs, particularly as it relates to secure and reliable command and control (C2) links and sense and avoid tactics. Therefore, the communications network in which the UAV operates plays an essential role in meeting security requirements and without its C2 link, a UAV cannot operate. Additionally, UAVs with unsecure and unproven C2 links are vulnerable to failure and even hijacking.
There are a number of C2 link solutions available that have been trusted for mission-critical applications by the government and defense industries. Additionally, there are wireless machine-to-machine (M2M) solutions providers that offer multiple frequencies for C2 links enabling UAV manufacturers and OEMs with a portfolio of options to deploy. While frequency options are important considerations, a C2 link is only as strong as the security capabilities it offers. With the appropriate security measures and data encryption capabilities in place, C2 links are better protected to thwart malicious attacks on UAV systems. Key considerations for secure C2 links that need to be integrated as part of the overall UAV solution follow.
Access Control Methods by Authentication, Authorization and Accounting
Proprietary wireless communication systems and devices (especially when they offer many “knobs” and configuration options to create private, user defined networks) actually offer a higher degree of security. But even those devices can be acquired, and most hackers are patient enough and can find out where to get them. Therefore, Access Control is one of the most important security features for wireless networking technology to prevent unauthorized access and intrusion.
Access control in cyberspace is the equivalent of the security guard at the main door of an office building that makes sure only people with the correct credentials can enter. So too, the goal of access control is to only allow network access by authorized devices and to disallow access to all others. Access should be authorized and provided only to devices whose identity has been established (authenticated) and whose placement on the network is approved in accordance with network plans, designs or policy.
This exemplifies a key security approach. The verification of identity, or Authentication, is based on the presentation of unique credentials to that system. The unique serial number of a wireless device for example (that hopefully can neither be “spoofed” nor counterfeited) may be such a unique credential.
Remote Authentication Dial in User Service (aka "RADIUS") is a popular method to provide centralized Authentication, Authorization and Accounting (“AAA”) to manage exclusive access to wireless communication networks.
Advanced Data Encryption and the Federal Information Processing Standards (FIPS)
The Federal Information Processing Standards (FIPS) are issued by the National Institute of Standards and Technology (NIST), as set forth by the Information Technology Management Reform Act of 1996 and the Computer Security Act of 1987. FIPS are a set of U.S. government computer security standards that define aspects of information security management, including document processing, encryption algorithms and other various IT standards.
Advanced Encryption Standard
In November 2001, FIPS Publication 197 announced the Advanced Encryption Standard (AES), a new cryptographic algorithm that could be used to protect electronic data. AES is “the” industry standard for data encryption and was developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen and adopted by NIST due to the need for a new data encryption algorithm. Today, AES is a Federal Government standard, trusted even by the NSA to protect sensitive information and maintain data privacy.
AES encrypted devices offer a variety of key strength options, including 128, 192 and 256. NIST has also defined 5 modes of operation for AES: Cipher Block Chaining, Electronic Code Book, Cipher Feedback, Output Feedback and Counter Mode. It is argued that counter mode is the most secure of the five because it uses a sequence of blocks to encrypt the data and is never repeated.
FIPS Publication 140-2
NIST issued the 140 series of FIPS Publications to identify the key requirements for cryptography modules. FIPS 140-2 validation consists of four clear levels of security, Level 1 being the lowest and each Level thereafter builds upon the next with additional security and/or trusted requirements, all the way up to Level 4. For example, Level 2 adds requirements for checking physical evidence of tampering, as well as role-based user authentication. Level 3 requires physical tampering resistance (further physical qualities making the module itself more protected against attackers attempting to gain access to sensitive information within the module itself) and a stricter identity-based authentication. Level 4 adds even more physical security requirements and requires an even greater robustness to the platform, in order to hold up against environmental attacks.
Manufacturers of unmanned systems and UAV platforms need to ensure the C2 links are provided not only by reputable wireless communication providers, but those with a proven track record of successful implementations in the field. These technology solutions must incorporate even the basic levels of FIPS and AES standards. This is because C2 data communication links with advanced encryption capabilities can help thwart hijacking attempts, signal interference issues and unauthorized access to critical data, all while ensuring dependable data transmission. These standards are tried and true and by incorporating these techniques into the C2 data communication link for unmanned systems, we can ensure the reliability necessary for introducing these platforms into the national airspace.
Final Considerations for Wireless C2 Link Technology
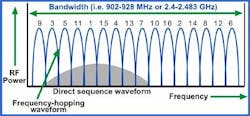
Wireless communication devices that leverage data encryption capabilities, adhering to FIPS and AES standards, are already heavily relied on for mission-critical government and defense applications, especially when it comes to unmanned systems and UAVs. As you can see above, there are a lot of specific security and data encryption standards to support the reliable transmission of C2 data. Furthermore, some wireless technologies that are proven to be reliable and secure in nature can further add to the overall data security scheme. For example, frequency-hopping spread spectrum wireless technologies can leverage coordinated, rapid changes in radio frequencies that literally “hop” in the radio spectrum, thus evading detection and the potential of interference. Furthermore, some leading wireless C2 link solution providers also can deliver multiple user defined cryptography keys (as many as 32 user-defined keys in some cases), allowing users to change key positions on demand.
With a secure C2 link in place, UAVs are far less likely to suffer from technical errors. This is a very important consideration because not only will there be more aircrafts operating in commercial airspace, but many will transport critical information where failure to operate is not an option. As the UAV industry continues to reach important milestones, there is clear indication that the FAA is moving forward as planned with the implementation of UAVs into commercial airspace. With this in mind, there needs to be a level of assurance that the unmanned aircrafts in our skies will be operating safely and benefitting many industries, which all starts with the C2 link.
Phil Linker is the Senior Product Manager for Government and Defense at FreeWave Technologies. Linker earned a Bachelor of Science degree in electrical engineering from Texas Tech. For more information on wireless command and control communication technologies, visit http://www.freewave.com or to discuss specific technology questions, contact [email protected].