LDRA Tool Suite features Code Checker for CERT C compliance, address safety and security vulnerabilities
WIRRAL, U.K., 8 Oct. 2015. LDRA, a provider of standards compliance, automated software verification, source code analysis, and test tools, designed the TBsecure module within the company’s LDRA tool suite to provide comprehensive, automated support for the Carnegie Mellon Software Engineering Institute (SEI) CERT C Secure Coding Standard. TBsecure checks for more than 200 CERT C rules, helping developers identify software safety and security vulnerabilities, officials say.
“The number and severity of attacks on mission-, business-, safety-, and security-critical systems has risen disproportionately with our increased dependency on these systems,” affirms Robert Seacord, a principal security consultant with the NCC Group and author of The CERT C Coding Standard (Addison-Wesley 2014). “Studies indicate that a majority of vulnerabilities in these systems can be traced back to a relatively small set of common programming errors. The CERT C Coding Standard enumerates these programming errors so that software testing and analysis tools, such as the LDRA tool suite, can be used to discover these problems before they are deployed in production systems.”
LDRA’s modular tool suite is used by product developers who require early insight into potentially exploitable safety and security vulnerabilities in source code, according to a company spokesperson. The TBsecure module uses current CERT C secure coding rules to find software issues that could leave products and systems open to security attacks.
TBsecure is designed to address security concerns in the increasingly complex and growing Internet of Things (IoT) market.
“As the number of IoT and other software-connected products in the world increases exponentially, so does the number of software security attacks. Just recently, for instance, a hack of Fiat Chrysler automobiles resulted in a recall of 1.4 million vehicles,” says LDRA Operations Director Ian Hennell. “To prevent financial losses and potential loss of life, software developers must take an automated approach to code quality improvement, fault detection, and other safety and security intelligence long before the product is manufactured and delivered to the marketplace.”
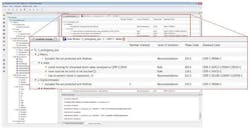
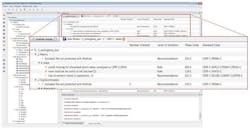
The LDRA TBsecure module, which plugs into the LDRA tool suite, shows code quality, fault detection, and avoidance measures through call graphs, flow graphs, and code review reports. Using TBsecure, managers, team workers, and developers can collectively monitor the implementation of safety and security metrics in their applications in an easy-to-read, intuitive format.
The CERT C Secure Coding Standard provides software development rules and recommendations designed to eliminate insecure coding practices and undefined behaviors that can lead to exploitable vulnerabilities. The application of the secure coding standard leads to higher quality systems that are more robust and more resistant to attack. Operating system and platform independent, the CERT Secure Coding Standards support popular coding languages including C, C++, and Java.
LDRA TBsecure supports a wide range of programming rules that can increase application security using the following classification of security issues:
Dynamic Memory Allocation (A): Dynamic memory management is a common source of programming flaws that can lead to heap-buffer overflows, dangling pointers, double-free issues, and other security problems. In particular, dynamic memory management encompasses allocating memory, reading and writing to memory, and deallocating memory.
Vulnerabilities (V): These rules are intended to eliminate insecure coding practices aside from those associated with dynamic memory. Examples of insecure coding practices include array indices out of range and dereferencing a null pointer.
TBsecure is available now.
For more than 40 years, LDRA has developed software that automates code analysis and software testing for safety-, mission-, security-, and business-critical markets. Working with clients to achieve early error identification and full compliance with industry standards, LDRA traces requirements through static and dynamic analysis to unit testing and verification for a wide variety of hardware and software platforms. LDRA is headquartered in the United Kingdom with subsidiaries in the United States and India coupled with an extensive distributor network.