Unmanned aircraft system safety, security, and autonomy through technology and standards evolution
Hardware and software technology, standards, and regulations combine to ensure the safety and security of current and future unmanned and autonomous vehicles and systems. An aerospace and defense industry veteran and security expert confronts current unmanned aircraft system (UAS) challenges, and offers advice to those engineering the autonomous future.
Intelligent Aerospace and Military & Aerospace Electronics editors sat down with Chip Downing, senior director of aerospace and defense at Wind River, an Intel company based in Alameda, California, during the Association of Unmanned Vehicle Systems International’s (AUVSI’s) Xponential conference and exposition to discuss the current state of unmanned aircraft systems (UAS) safety and security, encompassing regulations, standards, and technologies, including autonomous vehicle innovations.
FAA Part 107
One year has passed since officials at the Department of Transportation’s Federal Aviation Administration (FAA) in Washington finalized and instituted Part 107, the first operational rules for routine commercial use of small unmanned aircraft systems (sUAS) toward integrating UAS into the nation’s airspace. The new rule, which debuted in June 2016 and took effect in late August, offers safety regulations for unmanned aircraft drones weighing less than 55 pounds that are conducting non-hobbyist operations. Part 107 requires operators to keep the unmanned aircraft within their visual line of sight, allows operation during daylight and twilight if the drone has anti-collision lights, and imposes height and speed restrictions and other operational limits, such as prohibiting flights over unprotected people on the ground who aren’t directly participating in the UAS operation.
It does not require small UAS to comply with current agency airworthiness standards or aircraft certification, but it does call for the pilot to perform a preflight visual and operational check to ensure safety-pertinent systems, such as the communications link between the control station and the UAS, are functioning property. Operations not covered by Part 107, and not yet addressed by the FAA, include: operations over people, beyond line of sight operations, extended operations, flight in urban areas, and flight at night. “The FAA’s role is to set a flexible framework of safety without impeding innovation,” FAA Administrator Michael P. Huerta says. “With these rules, we have created an environment in which emerging technology can be rapidly introduced while protecting the safety of the world’s busiest, most complex airspace.”
A big disappointment is that it really did not address privacy or security. From a safety standpoint, Part 107 guidance requires operators to stay away from manned aircraft and people, and only fly during the day and only fly under 400 feet. It’s putting them in a box: Here’s where you can fly and here’s what you can do and if you’re around people, you shouldn’t be there. There is a hint of privacy, but not the strong privacy statements we’d like to have to protect anyone’s privacy at home or work or anywhere else. That’s something that still needs to be addressed. A lot of discussion needs to happen on that front and, most likely, we’ll have legislation in the near future. This is a challenging set of problems and the FAA made the right decision to publish Part 107 guidance before trying to address many of these thornier privacy and security challenges.
As for the safety and security of unmanned systems, Part 107 says you really don’t need to do a safety certification of that aircraft if it is a Part 107 commercial flight. You have to make sure aircraft is airworthy and that it is safe, but there’s no formal program to go through as far as the safety and security of that aircraft.
As you get bigger, go above 400 feet and above 55 pounds, want to fly at night, or do non-line-of-sight (NLOS) operations, you are going to have to go through safety certification – specifically because you are going to be in controlled airspace and potentially mixing with manned aircraft traffic.
Are you seeing a trend toward larger unmanned aircraft and heavier payloads?
We do see Wind River customers now emerging, some of them are evolving from the small UAS commercial space, that want to make a larger aircraft with a heavier payload or to fly outside of line of sight – say, a delivery vehicle or some other type of commercial platform. They are pursuing DO-254 and DO-178C certifications on those aircraft. I am not seeing this as a huge trend yet, but a few companies on the forefront are pushing this UAS certification rigor forward. The goal here is to get into a commercial space that’s separate and away from the Part 107 crowd, which is now flooded with lots of different aircraft. AUVSI proved that; it’s a marketplace now for unmanned systems.
Are more people opting to build their own or customize unmanned vehicles?
I use the Intel white box analogy: Many years ago the way to build your personal computer was to buy the parts and assemble it yourself. Just a few years ago the UAS industry was in this zone – many parts from many vendors, but no total solutions from any one vendor. But just like PCs where companies like Dell, Compaq, IBM, HP, and many smaller companies began selling fully-assembled white box PCs, the UAS industry now sells fully assembled airframes from DJI, Parrot, Yuneec, PrecisionHawk, Insitu, and Intel with multiple available payloads/applications. So we are now in the white box phase of sUASs, with a wide marketplace of components and platforms you can buy and customize and put a wide range of payloads onto.
It’s something everyone likes to ignore, but security now becomes more critical when you start having heavier payloads and heavier aircraft. How do you actually qualify that as safe and/or secure? There are no regulations to do that yet; certainly, with Part 107 you don’t have to. At some point, we should start to talk about: How do you secure that flight? How do you make sure that data, especially if it’s private data or possibly impinging on someone’s privacy, remains secure on that aircraft and the aircraft operator’s control station? I haven’t seen security be a key feature of these new UASs, but I expect to see that soon.
aircraft for carrier operations. Wind River VxWorks is its primary computing environment.
Where can we start, even before there’s a requirement?
Wind River has built in security across our product portfolio, and what we’re doing is saying, “Here are some basic capabilities that you can build into your aircraft.” And typically it’s not just a platform; there’s going to be some end-to-end security that must be factored in. Wind River also does security assessments for many of our customers to help determine the vulnerabilities in their solutions; it’s a very popular concept. It’s a hard thing to say: Is this aircraft secure? Is this system secure? Are the communications secure? If you do a security assessment, you can figure out what is vulnerable and what has high risk, and then you can address that with both commercial products and services.
We’re working on a Security Technical Implementation Guide (STIG) for each product – starting with our VxWorks real-time operating system (RTOS) and Wind River Linux. This will be a first for the RTOS industry; Wind River has invested in creating a formal guide to implement or connect to network securely. That’s one piece in a larger security puzzle, and an important first step. They have a safety manual for industrial certifications; this really is a security manual for people who care about security on their connected platforms, in any industry.
There’s a big focus on cyber safety and security, especially given the rise of ransomware and availability of ransomware kits. Are FAA, NASA, and Department of Defense systems, as well as manned and unmanned aircraft avionics, susceptible to such threats?
Absolutely – even though a lot of these government entities have good security systems, they are constantly improving. As threats evolve, security is going to have to evolve along with that. I think perhaps the affected companies had not stayed current with some of the most recent security patches and that led to some of these intrusions. That can apply down through the entire communications chain – whether a manned or unmanned vehicle or some type of federal facility.
evaluating UAS air traffic management (UTM) technologies.
There are lots of capabilities Wind River has and virtualization is one of those very good capabilities that should be deployed. The term ‘secure RTOS’ comes up a lot and it’s not wrong, it’s just that it’s only a small piece of the puzzle: secure capabilities within an operating system (OS), whether it’s Windows or VxWorks or any other type of platform.
Everyone would like to say, ‘Oh just install a firewall or virtualization and you’re safe and secure.’ It’s just not that way anymore. These are wide open systems and there are lots of different ways to penetrate these systems. It is important to take a holistic approach. It’s very similar to the approach the FAA takes on an aircraft. It’s not just an operating system or a wire or board, it’s the entire system, it’s the entire aircraft. How do you prove that it’s safe and/or secure?
What actions can we take now to protect the security of these systems and avoid further/worse threats?
A security assessment is the right first step; it is the best way to look at these types of vulnerabilities, to find out what is vulnerable, what needs to be updated, and what types of additional security capabilities need to be installed on the platform.
You have to constantly stay up to date with security patches coming from any vendor on these platforms; it is probably the number one way you can protect yourself today. Occasionally, we will generate a patch for our operating systems that we release to our customers.
Important to note though, in many cases the biggest errors are not errors with the software or the operating system, it is how that system was deployed. How did you configure that system? Did you have open access on your interfaces? Many companies with embedded devices don’t pay attention to securing that network interface. Ten years ago, not much focus was put on that; today, we all realize that any type of connection, whether a USB or network connection, has a security risk behind it and we need to figure out a strategy to protect that resource.
When running multiple systems on a virtual machine and one of those systems is compromised, how are the others kept safe?
Virtualization especially on modern platforms that have hardware virtualization assist, like VT-x and VT-d from Intel, protect quite well. They encapsulate each environment with hardware protection, so it’s not software that’s providing that protection or software managing it; there’s hardware virtualization assist intellectual property that helps secure that. So if something does occur on one of the virtual machines or guest OS environments, it tends to be contained in that virtual machine environment.
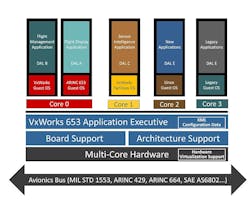
At Wind River, we have RTCA DO-178C certification platforms that use this virtualization assist – we take that to its fullest. To augment this we also deliver a technology called robust partitioning that really proves that if a partition or guest OS environment does have a problem, it doesn’t impact other guest OS or partitions on that platform. Using that in reverse, if you want to update a guest OS or partition on a platform using our technology, you do not have to retest the entire platform, only the scope of the change. This is the reason why our VxWorks 653 product is so popular – it saves the avionics industry significant test and retest investments.
It’s easy to throw a bunch of applications onto some type of virtualization platform. Per FAA DO-178C guidelines, if you change one line of code, you must retest the entire platform because the FAA has proven that there will dependencies. With our COTS certification evidence product, we go to great lengths to isolate the operating environment away from each of the partitions or guest operating environments because if one must retest the entire platform, it can get very expensive or untenable to create a consolidated software-defined environment with safety requirements. One simply cannot afford to do consolidation of many applications, because any change on the application or operating environment will require a complete retest of the entire platform. On large programs, it can save you billions of dollars over the life of that program if you have this technology that restricts the testing of changes to the scope of the change.
Are very strict safety and security regulations impeding technological advancement?
If you take the latest application technology and throw it on a virtualization platform that does not have a robust partitioning strategy, are you advancing the technology in a next generation system or are you introducing new and unknown vulnerabilities? You may have just created a bigger security and safety risk for that platform because you don’t know the impact of putting a change in any of the guest OS environments or any type of change in that platform. Part of safety and security is knowing what the impact of the change is. Customers that use VxWorks 653 will do an analysis: If I change this one component, what is the impact of that change? What is the scope of that change? It’s actually very forward-looking and drives greater responsibility throughout all of the platform components. The casual way of integrating systems leads to poorly deployed systems, with a lack of knowledge of the impact of change, driving poor safety and lax security into the platform.
Does a shining example of UAS safety and security exist today?
Commercial aerospace has the right rules and the right support infrastructure with the FAA. They tend not to have a lot of unmanned systems flying under FAA guidelines, but they certainly have the infrastructure to make that happen. Defense departments of larger nations have a similar focus now on using commercial-grade, FAA-style certification standards to increase the safety and security of platforms. That’s especially important if you’re purchasing a platform from another country or another vendor: How do you qualify this platform as something that could be safe and/or secure? If you require safety or security artifacts for that platform, you’re increasing the probability of having higher platform quality and therefore fewer deployment problems.
The nEUROn Unmanned Combat Aerial Vehicle (UCAV) demonstrator, the first large-size stealth platform designed in Europe, was designed and produced by Dassault Aviation and six European nations (France, Italy, Greece, Sweden, Spain, and Switzerland) with the significant objective of demonstrating the maturity of technologies by delivering modular safety critical avionics systems running on COTS-based on-board computers — and standardized on the Wind River VxWorks 653 operating system.
Traditionally, military controlled the unmanned space with large unmanned air systems, and were somewhat concerned about operational safety and security, but I don’t think this segment could be looked upon as a shining example. Commercial aircraft manufacturers and commercial airlines certainly know how to field safe and secure systems, and have an existential concern for safety and security. As new unmanned technology comes out, autonomous vehicles will be the place with the highest level of innovation; they have a great opportunity to build new systems from the ground up with safety and security in mind.
The biggest challenge for unmanned systems developers is to create systems that can operate autonomously outside of restrictive Part 107 environments, creating very unique and powerful value. These systems will need to prove both hardware and software robustness using safety standards like IEC 61508, DO-178C, and ISO 26262. Wind River and Intel are well positioned to serve this larger, higher-value market expansion.
Intel's Falcon 8+ advanced, commercial-grade unmanned aerial vehicle is designed for professional use. It is designed to be stable and rugged enough to work in high winds, be resistant to magnetic field disturbances for accurate data capture, and offer electronic system redundancy, including autopilot and battery redundancies.
Intel is pushing hard in the autonomous vehicle arena. Is Wind River involved?
Intel is acquiring and/or developing the technology for autonomous autos, or driverless or self-driving cars, and making large investments. Wind River has an autonomous framework, Wind River Helix Chassis, which you can build up with a combination of Wind River and Intel components for the next-generation electric or autonomous car.
Intel is also taking a bold next step – creating functional safety processors. The first one, released in December 2016, called the Intel® Xeon® Processor D-1529 for industrial IEC 61508 certification solution, which has already achieved industrial certification IEC 61508 SIL 2. Intel is also making new chips which will be targeted toward automotive and other platforms that will have similar functional safety certifications. Intel is going through the challenging process of understanding how to build next generation microprocessors to be safer and more secure. That’s a huge change in the industry, and will force other chip manufacturers to come up with competitive solutions.
The nice part for Wind River is that we now have a foundation for a joint hardware-software commercial-off-the-shelf (COTS) functional safety solution. A customer can start with one of these functional safety processors and put one of our operating systems with COTS certification evidence on top of that, and now you have a combination of safety artifacts that can be readily deployed for safety-critical systems. Traditionally, the hardware side especially was required to go through RTCA DO-254 avionics hardware certification. We can now compress that time if we have all the artifacts to do that. That’s not planned right now; the initial certifications are for IEC 61508 for industrial and ISO 26262 for automotive, but those basic foundations could be augmented with other work to get to DO-254 and other hardware safety certifications.
Autonomy
Downing presented a thought-provoking technical paper, entitled “Next-generation Automobiles Will Look Like Manned and Unmanned Aircraft,” during a keynote at AUVSI’s Xponential. “Future automobiles will have electronics systems that closely resemble commercial aircraft systems, which optimize safety, security, reliability, and availability,” the paper reads.
The first robotic copilot helped fly and land a Boeing 737 simulator. If the future of commercial air transport is unmanned, or even all-electric, how important is the OS and security?
If you have autonomous systems, you really have to go the extra mile.. You have to do more than what you would typically do for a manned system -- in a manned system, you have a person who can make good or bad decisions. With autonomous systems, the expectation is that it will be far safer, far more reliable, and have better security than a purely manned system. The expectation is that autonomous systems will make better decisions with better situational awareness than a manned system.
If you think about communications, right now we have a lot of voice communications, which have a high error rate, in a manned environment. There’s not going to be voice commands for an autonomous system. It’s going to be some type of electronic command that will be fully traceable, and also something that can be interpreted by both people and machine -- and, most importantly, the understanding between the communicating parties should be at the 100 percent level. Today, only roughly 35 to 50 percent of voice communications are truly understood. It has also been proven that automatic landing systems are typically better, more reliable, and more precise than manned landings. We still do manned landings to keep ratings up for pilots, but if you look through literature, you can see that unmanned landings are very accurate, typically within inches of each other on a runway – that’s just about impossible to do as a human.
Why are you such a big proponent of the autonomous vehicle market learning or borrowing from the aerospace community?
Future vehicles will look like manned and unmanned aircraft. There’s already an infrastructure of extremely high safety, of very rigorous and good security in the commercial aerospace industry. The autonomous car industry should leverage that capability – like ARINC 653 time and space partitioning technology - into autonomous vehicles. In many cases, autonomous vehicles on the ground are going to require higher levels of safety and higher levels of security than those that fly in controlled airspace.
When you think about aircraft, even when it’s backing up from the gate, you have professionals on the ground saying ‘big aircraft here – look out.’ In the air, it’s in controlled airspace where there are flight rules, five miles of separation, and lots of ways to keep aircraft separated. In ground vehicle operations, none of that infrastructure exists, plus you have unplanned activities: a puppy dog walking across the street, or a child running out in the street after a ball, or a police action, or something on the ground occurring that is unexpected. So these autonomous vehicles have to be a lot smarter than an aircraft, whether unmanned or manned, and it has to react faster and really be flawless. Ground operations are simply more unpredictable.
If you think about it, traditionally we’ve tolerated killing 40,000 people a year on our roads in the United States alone – globally, it is probably 10 times that number – because there’s a human you can always blame. And most of the time these accidents are based upon reckless driving, drunk driving, and distracted driving. With an autonomous vehicle, there’s no human to blame. It will require the manufacturer and operator to have higher responsibilities than they have today and to have a real security and safety plan, so if something does happen, industry can figure out how to fix the problem. In addition the precise chain of responsibility can be defined.
We talked earlier about privacy; this is not a privacy issue, it’s a liability issue. A good way to constrain liability is don’t get into accident. If you do, have a good story about how you did everything in your power using safety and security standards to protect that vehicle and operate in the safest, most secure way possible. Not too many people are thinking about that yet.
What do you propose for autonomous vehicle regulations?
Something I proposed at AUVSI last year: It’s great to have autonomous vehicles generate another set of safety standards, but it’s a lot easier to take what exists in the avionics field, that has a very deep and rich industry support for safety and security, and just use that on an autonomous ground vehicles. These avionics platforms support mixed levels of criticality, which enables platform consolidation. On an aircraft, that’s always been important because every time a different vendor brings a box and its federated architecture on an aircraft, it adds size, weight, and power constraints (SWaP). Platform consolidation using industry standards like ARINC 653 reduces SWaP. The automotive industry, where most of the suppliers bring their own compute platform, need to undergo the same evolution as the aircraft industry, where separate hardware-defined components are forced into a software-defined solution on a common, shared compute platform that safely consolidates multiple supplier capabilities.
Going to an integrated modular avionics (IMA) environment is what drives the efficiencies of the Boeing 787 Dreamliner. The Boeing 777 actually pioneered this IMA concept many years ago – you now have a software-defined architecture on a shared compute platform on an aircraft versus bringing a box or piece of hardware, each of which requires wiring, cabling, and maybe a different redundancy strategy. You now put this on a common core environment with a proven triple-redundant environment. All these functions that used to be a piece of hardware are now just software applications that plug into different ARINC 653 partitions on this platform.
This transition from hardware-defined to software-defined in avionics is based upon a standard called ARINC 653. The automotive industry is still a federated environment with a very complex supply chain; everyone still tends to bring their own box to the OEM party and that’s why you have 60 to 100-plus processors on each car now. When you have that type of environment, the wiring harness is now the second most complex component on a car because you have all these different boxes that need to be supported on a given vehicle. So it makes perfect sense to do some platform consolidation, making these different functions software-defined just like on a Boeing 787 Dreamliner.
The Defense Advanced Research Projects Agency (DARPA) Aircrew Labor In-Cockpit Automation System (ALIAS) program has demonstrated its automated flight capabilities with various flight scenarios in a Boeing 737 simulator. Aurora Flight Science’s ALIAS technology demonstration system is designed to function as a second pilot in a two-crew aircraft, enabling reduced crew operations while ensuring that aircraft performance and mission success are maintained or improved. On a Boeing 737-800NG simulator at the U.S. Department of Transportation’s John A. Volpe National Transportation Systems Center in Cambridge, Massachusetts, ALIAS showcased its ability to use the existing 737 auto-landing system to autonomously land the aircraft safely in the event of pilot incapacitation.
The tendency of the automotive industry is to say: ‘I don’t want to use avionics because it is going to be too strict for an autonomous vehicle.’ I say, ‘No, that’s exactly what you want.’ You might think you are saving money, but really you’re losing money because a lot of cities that embraced autonomous vehicles have now stopped them because of accidents or other types of incidents. You’re actually delaying the adoption of autonomous technology because you haven’t adopted a good safety and security approach; you don’t have a platform that is based on avionics or some type of proven safety strategy.
I call it the mad cow disease of the automotive industry – the denial that you need to have high levels of safety to make autonomous vehicles successful is costing billions of dollars. That affects the entire industry. It costs billions. You have this huge cost you don’t measure because you looking too close to ‘I’m going to make an extra 50 cents by doing this’ instead. A lot of people don’t want to hear that but it’s a denial about what you really need to go do and, as you deny that, you push out the adoption and acceptance of autonomous vehicles. Use proven safety and security standards when possible – this accelerates time-to-market and removes the unprofitable process of testing and proving a new standard that adds little value to the end product.
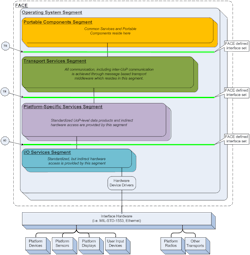
Future Airborne Capability Environment (FACETM)
The goal of the FACE initiative is to reduce software development and integration costs and reduce time to field new avionics capabilities. The FACE approach establishes a common computing software infrastructure supporting portable, capability-specific software components across Department of Defense avionics systems. For more information see: http://www.opengroup.org/face.
Do you see greater investment in open architectures, commercial off-the-shelf (COTS) products, and reuse initiatives like the FACE and SOSA™ (Sensor Open Systems Architecture) initiative in the unmanned/autonomous/robotics community?
Open architecture designs are here to stay. System complexity, cost, and manageability are driving this trend. Reuse and rapid insertion as defined in the context of the FACE and SOSA initiatives are just getting into production mode, with Harris, Honeywell, Rockwell Collins, and Wind River leading the charge; all four companies have completed FACE conformance certification tests for their industry-leading avionics solutions.
The latest FACE Technical Interchange Meeting (TIM) sponsored by the U.S. Air Force is one more indicator that the U.S. military is now driving open standards into new program designs. Standards like the FACE and SOSA Technical Standards, along with industrial safety standards serving a wide range of platform segments, will drive far greater levels of interoperability and allow systems deployed today to constantly upgrade their competitive edge for many years to come. Static, proprietary systems of the past will have to open up to maintain their relevance to future missions.
Wind River has announced FACE certification for VxWorks 653. What is the significance of this certification?
To start, the FACE Technical Standard and Business Strategy are the culmination of many years of hard, conscientious work by hundreds of dedicated engineers to create an open standard for critical airborne and other mobile platforms and a business case to ensure its adoption. This standard was designed from the beginning to enforce certified conformance to reduce the risk and cost of multi-vendor platform integration.
Wind River’s VxWorks 653 platform is the first Operating System Segment (OSS) to be certified conformant to the FACE OSS Safety Base Profile, enabling the mix of both ARINC 653 and POSIX® applications on a robust, proven safety-critical avionics platform. This enables our customers to immediately use VxWorks 653 on programs with FACE requirements (read more at http://blogs.windriver.com/wind_river_blog/2017/03/vxworks-653-platform-achieves-first-face-operating-system-segment-certification.html).
How has FACE evolved, and does it apply to UAS?
I have been working with the FACE standard since its inception seven years ago. It is now starting to roll out; it’s in what I call production mode. The FACE Technical Standard and Business Strategy are complete, and over 50 programs now reference FACE as a requirement. The more than 50 public government procurements with FACE requirements today include the U.S. Air Force, U.S. Army, U.S. Navy and Naval Air Systems Command (NAVAIR), Defense Advanced Research Projects Agency (DARPA), and U.S. Special Operations Command (SOCOM), so this standard is now well-entrenched into U.S. military procurement operations. There are also foreign militaries that are standardizing on FACE. (For more, visit http://www.opengroup.org/face/procurements.)
There are also many other programs that are not public. These tend to be quite large programs with challenging multi-vendor integration requirements, so the FACE approach is a logical choice to reduce program risk, reduce platform costs, and accelerate time to deployment.
It is exciting and gratifying to see that evolution of the standard. The FACE initiative is really adopting what the commercial aerospace industry has done for 20-plus years, using industry standards like ARINC 653 and open standards like POSIX. To me, that’s very healthy as we get into a high reuse environment, which was not that important with just manned aircraft, but as we have an increasing number of unmanned aircraft, we’re going to want to have a high reuse environment. If you can take applications or payloads from one UAS platform and put it on the next UAS platform and not have to support a large systems integration effort, then you have high reuse with high platform efficiency. As the FACE approach matures it should drive very modest systems integration efforts, similar to loading an Android or iOS application, and work very quickly on a new platform. This has very high value in future airborne platforms.
What’s on the horizon, technologically speaking?
We’re seeing this explosion of a PowerPC-centric industry to one using PowerPC, ARM, and Intel coming up. It makes it a very rich processor choice for customers. All these chips are getting more complex, and the complexity of certifying them for both safety and security is going up. That’s a challenge to which we’ll have to embrace and adopt..
Wind River has just released our first multi-core certification evidence package for the PowerPC processor that has a true virtualization foundation and supports multiple guest OS environments. It will be a big first in the industry where we have support for the ARINC 653, POSIX, and FACE Standards, and also a guest OS environment like Linux. We are seeing the power of hardware increase the capabilities of the software on top of it, and enabling it to be deployed in mixed criticality environments. We’re going from a fairly simple partitioning environment to one that’s more complex and uses hardware virtual assist to make multi-core systems more safe and secure.
One of the things ARINC 653 has done traditionally very well is, because of its robust partitioning, is enable the deployment different levels of safety criticality applications on a shared compute platform. Typically those were simplistic environments, because the process of safety certification was high and the processor itself couldn’t support something complex like a Linux guest running next to something critical, like a flight control environment. It didn’t make sense, and sometimes the real-time performance would suffer greatly.
Now with a multi-core system, you can put different levels of safety criticality on their own core and run a guest OS environment on different cores, so the complexity and interference is diminished and controlled by hardware. This hardware virtualization assist makes sure the microprocessor resources are secured and dedicated to those different operating systems and there’s no interference from other operating environments, partitions, and/or virtual environments. That would be impossible to do using traditional technology using an MMU for separation and control; you need to have hardware virtualization assist to make this all work.
You have gone to AUVSI events for more than a decade. What long-term trends are you seeing at these shows?
Ten years ago, this event was much smaller, and most of the suppliers were showing highly proprietary and/or experimental systems. Today, it is a true unmanned marketplace with a wide range of technologies based upon open standards serving the unmanned industry, including unmanned air systems, ground vehicles, autonomous cars, and industrial/robotic systems.
It is great to see these technologies blossom into ready-to-use industrial products that can support strict safety and security standards. Open standards have boosted innovation in this space, but have not eliminated the need for robust systems that simply cannot fail. It’s imperative to have both components, this is why it is fascinating to see the designs presented on the show floor.
CoreAVI, Presagis, and Wind River introduced an integrated multi-touch avionics graphics screen. What makes it unique?
Avionics suppliers are challenged by providing any type of dynamic capability due the cost and risk of certification. This integrated solution stack enables multi-touch screen utility, similar to Android and IOS devices, in a ready for certification solution stack.
There are three distinct components in this multi-touch avionics solution:
· A graphical display application generated by Presagis’ VAPS XT design tool,
· A Wind River real-time operating system, either VxWorks or VxWorks 653, which controls the execution of the applications, and
· A graphics driver library from CoreAVI that processes OpenGL SC (Safety Critical) commands to be displayed on the touch-screen.
This integrated solution can save money and reduce program risk for avionics development because both Wind River and CoreAVI products are available with development tool chains and commercial off-the-shelf (COTS) certification evidence, the benefits of which are well understood by the industry.
These two COTS certification stack components are augmented by Presagis’ VAPS XT application development solution for user interfaces that generates ready-for-certification code automatically to implement the design created in the editor, and to get it deployed and certified in a shorter timeframe. The generated application interfaces to CoreAVI’s driver and to VxWorks or VxWorks 653. The result is applications that are superior to those coded by hand, are more easily created and updated, and which can be deployed on any platform.
The power of VAPS XT is that it allows focus on model design rather than the writing of source code, shortening development cycles, and reducing software development costs. Presagis provides a Certification Kit for the tool which, when combined with the COTS certification evidence from CoreAVI and Wind River, reduce program risk significantly, and the time-to-market for certified products is compressed.
The COTS certification evidence from Wind River and CoreAVI support RTCA DO-178C DAL A solutions. The Presagis VAPS XT tool is qualified under DO-330 TQL-1 for its code generator and DO-178C DAL A for embeddable code.
Why was Intel CEO Brian Krzanich, who delivered a keynote at Xponential, selected to chair the FAA's Drone Advisory Committee, which provides the FAA with advice on key UAS integration issues by helping to identify challenges and prioritize improvements?
Brian Krzanich is the logical choice for this position to create broad support for an UAS and sUAS integration strategy and vision. He is passionate about unmanned and autonomous systems and understands the complexities of bringing these types of product to commercial fruition, and has proven that with Intel’s internal development and external acquisition. He also has the energy and drive to push these new initiatives through a large organization, making Intel a perfect fit to shape this industry to solve tomorrow’s challenges.
Chip Downing, senior director of business development for aerospace and defense at Wind River Systems, is a 20-year veteran of the embedded systems industry, a pioneer in safety certification for commercial real-time operating systems (RTOS), and chair of the Future Airborne Capability Environment (FACE) Business Working Group Outreach Committee.
The theme of this year’s Xponential was “Shape Tomorrow”. How are Wind River and Intel shaping tomorrow?
Next-generation systems will need to support autonomy and safety. Intel is leading here – they have developed and/or procured technology to support autonomous systems. Two examples of this are the recent purchase of Mobileye, a leader in computer vision for autonomous driving technology, and Yogitech, a functional safety (including Advanced Driver Assistance Systems or ADAS) firm to enhance the safety of transportation and factory systems.
Intel has also introduced functional safety parts, like the Intel Xeon processor D-1529, the first Intel processor designed for industrial IEC 61508 functional safety certification. Released last December, the Intel Xeon processor D-1529 has received TÜV IEC 61508 Safety Integrity Level (SIL) 2 certification. Functional safety parts derived from standard Intel technology accelerates the use of complex processors into safety-critical systems.
Wind River, with a portfolio of software products that enables the development of functional safety solutions and proven track record of ensuring the reliability of critical systems, is a natural complement to these functional safety hardware foundations. Both the hardware and the software can be taken through to the same level of functional safety certification. Our lead operating system, VxWorks, has some specific aspects that are designed for safety, such as allowing users to design a system that would contain all the characteristics you need in terms of separation of applications. This includes failure modes, or advanced time partitioning for multiple applications of different criticality levels, protecting the system from errant applications.
Now both companies can deliver COTS safety products into next generation systems that will shape tomorrow’s technology. As part of Intel, Wind River is in a great position to drive complete software and hardware solution capabilities that will accelerate the adoption of the Internet of Things (IoT) in critical infrastructure domains. By providing leading solutions in the cloud, the network, and at the edge, we can address the entire IoT deployment cycle.