Grier Forensics helps law enforcement, military cyber security speed analysis of captured hard disks
NIJ officials have awarded a contract to Grier Forensics to develop ways of significantly increasing the speed with which large amounts of data are forensically processed and stored.
Grier Forensics has developed software to speed up the forensic image acquisition process at least by a factor of three so that a 1-terabyte hard disk that at one time took 10 hours to process now takes around three hours, company officials say.
Grier experts developed this software originally under sponsorship of the U.S. Defense Advanced Research Projects Agency (DARPA) in Arlington, Va., as part of the DARPA Cyber Fast Track program.
The funding from the NIJ will enable Grier Forensics to mature the software such that it is ready for use in the field by law enforcement.
"There are huge amounts of data because hard drives are so cheap and so ubiquitous," says Jonathan Grier, principal at Grier Forensics. Investigating cyber crimes or enemy cyber attacks on U.S. military and other government computer networks "can involve going through lots and lots of hardware, and lots and lots of disks."
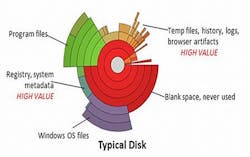
Traditional cyber forensics essentially images and analyzes everything on a suspect hard drive, without regard to data that might be relevant to the investigation, data that isn't, or even empty space on the disk. That approach can waste a lot of time and drag out cyber investigations.
Grier says his company is trying to take a smarter approach to analyzing impounded hard disks. "Most drives are never completely written to," he explains. "We can identify the parts of the drive that have been used and sift out the parts that have never been used."
That way, instead of taking a bit-for-bit copy of the entire drive, Grier experts have found ways to zero-in on data recorded on the drive that might be relevant to an investigation, bypassing non-interest portions like unwritten disk space and operating systems.
"If we can sift out the parts that are not important, we can reduce the time it takes to gather relevant data by a factor of 10," Grier says.
Related: Army invites industry to demonstrate COTS tactical biometrics technology
This ability has broader-reaching implications than law enforcement investigations of suspected cyber crime, Grier says. It also has the potential to help U.S. military cyber warriors take the fight directly to the enemy in the field.
"In Afghanistan, for example, operations are involving more and more computer systems, but deployed personnel don't have the ability to investigate cyber intrusions on base; the amount of data is too large to ship over a satellite."
Enabling military cyber security experts in the field to perform quick analyses of captured computer hard disks could help them act on time-sensitive intelligence data that might not otherwise be possible with traditional computer forensics. "In investigations we want to get days down to hours, and hours down to minutes," Grier says.
His overall goal is not to replace traditional cyber forensic practice, but instead to fit into existing procedures. "We want to be compatible with existing investigation tools and plug right into to them," Grier says. "We would like to see this technology folded into the tools that are already used."
For more information contact Grier Forensics online at www.grierforensics.com, or the National Institute of Justice at www.nij.gov.