Enhancing Network Security with MACsec (IEEE 802.1AE)
Until recently, fiber optic network interfaces had a significant advantage over traditional copper Ethernet networks when it came to security. Because fiber optic cabling transmits data as light particles, it natively provides a layer of protection from interception. Conversely, twisted pair copper cables transmit data using electrical signals that emit radiation, making transmissions vulnerable to eavesdropping and tapping.
However, IEEE 802.1AE (also known as MACsec) crypto has somewhat levelled the playing field between copper and fiber optics in regards to security, and positioned copper wiring for some applications where optical wiring was formerly the sole contender. First standardized in 2006, but not fully embraced for another decade, MACsec is now seeing increased adoption, driven by the fact that MACSec support was added to the Linux kernel (as of kernel 4.6) in 2016.
https://www.curtisswrightds.com/news/blog/enhancing-network-security-with-macsec.html
What is MACsec?
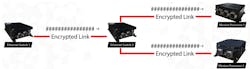
Preventing disruption and data loss arising from transmission and reception by unauthorized devices is a required network capability in today’s defense applications. In order to provide this protection, the MACsec standard enhances security for network traffic by identifying unauthorized LAN connections and excluding them from communication within the network. The protocol authenticates nodes through a secure exchange of randomly generated keys, ensuring data can only be transmitted and received by MACsec-configured nodes. By assuring that a frame comes from the station that claimed to send it, MACSec can mitigate attacks on Layer 2 protocols.
In addition to data origin authentication, MACsec provides optional point-to-point, Layer 2 encryption between devices on a virtual or physical local area network (LAN). In most instances, this encryption on Layer 2 eliminates the need for a dedicated LAN security device, which is helpful in reducing the network’s overall footprint in size, weight and power (SWaP)-constrained applications.
As well, each MAC frame in a MACsec-enabled LAN carries a data integrity check value to ensure accuracy and consistency throughout transmission, and all frames copied from the LAN cannot be resent into the LAN without detection
How is MACsec Enabled?
The main use case for MACsec is to secure a LAN with multiple machines. In order to implement MACsec functionality between a switch and connected endpoints (such as PC clients), devices use a standardized negotiation protocol called MACsec Key Agreement (IEEE 802.1X-2010).
MACsec vs IPsec – What’s the Difference?
MACsec is for authentication and encryption of traffic over Ethernet on Layer 2 LAN networks. Alternatively, for Layer 3 networks, IPSec is used. Since MACsec and IPsec operate on different network layers, IPsec works on IP packets at Layer 3, while MACsec operates on Ethernet frames at Layer 2. Thus, MACsec can protect all Dynamic Host Configuration Protocol (DHCP) and Address Resolution Protocol (ARP) traffic, which IPsec cannot secure. On the other hand, IPsec can work across the wide area network (WAN) for routers, while MACsec is limited to switches or end-nodes on a LAN.
As copper cabling has matured, the MACsec protocol has strengthened its competitive value against its fiber optic counterpart. Still, there are many preconceived notions about both interface types when it comes to their strengths and weaknesses for military and aerospace applications.
MACsec-enabled switches encrypt Ethernet traffic between LAN devices to prevent data loss or transmission/reception by unauthorized devices
About the Author